Knock Knock Mac OS
adminMay 03 2021
Knock Knock Mac OS
'Who's there?' See what's persistently installed on your Mac.- Knock Knock Mac Os Download
- Knock Knock Mac Miller Cover
- Knock Knock Mac Os Catalina
- Knock Knock Mac Os X
Malware installs itself persistently, to ensure it is automatically executed each time a computer is restarted. KnockKnock uncovers persistently installed software in order to generically reveal such malware.
Runs on: WinXP, WinVista, WinVista x64, Mac OS X, Windows2 The Knock Project v.092305 The Knock Project is a collection of security tools providing increased client/server authentication. Knock-Knock is an horror themed adventure game developed and published by Ice Pick Lodge. The game has been devised by the developers from 19 mysterious files, sent to them by an unknown figure via email; they were asked to finish the project using the information stored in these files, with the only catch that they had to include everything in the files, but designing it was.
Current version: 2.3.0 (change log)
Zip's SHA-1: 8CF5F309520DD2B3DF32726FF8EA845D60E29D13
Note:
For details about persistence & OS X/macOS malware, see my paper:
For details about persistence & OS X/macOS malware, see my paper:
To use KnockKnock, first download the zip archive containing the application. Depending on your browser, you may need to manually unzip the application by double-clicking on the zipped archive:
To run the application and begin a scan, simply double-click KnockKnock.app.
Note:
On recent versions of macOS, KnockKnock will prompt for 'Full Disk Access':
This is optional, but will allow KnockKnock to perform a more comprehensive scan.
For more information on 'Full Disk Access', see: 'Full Disk Access and Why You Shouldn't Be Afraid of It'
On recent versions of macOS, KnockKnock will prompt for 'Full Disk Access':
This is optional, but will allow KnockKnock to perform a more comprehensive scan.
For more information on 'Full Disk Access', see: 'Full Disk Access and Why You Shouldn't Be Afraid of It'
Press the 'Start Scan' button to instruct KnockKnock to scan known locations where persistent software or malware may be installed. By design, KnockKnock simply lists persistently installed software. Although by default signed-Apple binaries are filtered out, legitimate 3rd-party software will likely be displayed.
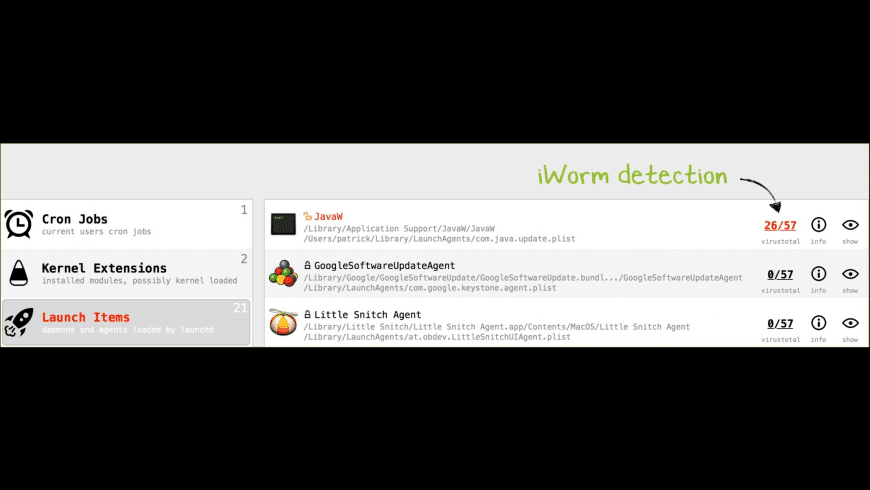
The left-handle table contains the categories of persistent software that KnockKnock scans. Each row contains the name and brief description of the category, and the number of detected items. Clicking on any of the categories will display the items for that category in the right-hand items' table.
Each row in this table contains the name of the detected item, an icon indicating whether it belongs to Apple, , or a 3rd-party (but still signed) , or is unsigned , its full path, and then various informational and actionable buttons. These buttons provide information about item's VirusTotal (anti-virus) scan results, general information about the file, and the ability to view the item in Finder.
If the item is an executable binary, KnockKnock automatically queries VirusTotal with a hash of the binary in order to retrieve any information. While VirusTotal is being queried, this button displays '■ ■ ■'. Once the query is complete, the title of the button is automatically updated with either the detection ratio, or a '?' if the binary is not known to VirusTotal.
With the query complete, the button can be clicked to reveal a popup containing VirusTotal-specific information about the file. If the file is unknown, clicking the 'submit?' button will submit the file for analysis. Known files contain a link to the full analysis report and a 'rescan?' button that will rescan the file.
If known malware is detected, the item's name and VirusTotal button will be highlighted in red. Moreover, the name of the category will be similarly highlighted:
The 'info' button will display detailed information about the item, including its hash, size, plist (if applicable), and signed status:
Knock Knock Mac Os Download
As of version 2.0, if the item is persisted via a property list (plist), one can click on this to view it's contents:Back to the main window, clicking on the final button ('show') in the item's row, will reveal the item in a Finder window.
Knock Knock Mac Miller Cover
To control or influence the execution of KnockKnock, click the 'gear' (preferences) icon found at the bottom left of the window. This will display KnockKnock's preference's window (note, this Window is also displayed via the 'Preferences' menu item):
- 'show os/known items':
Display everything it finds (by default it filters out signed Apple and white-listed items). - 'disable update check':
When KnockKnock is launched, disable the automatic check for new versions. - 'disable virustotal integration':
Do not query VirusTotal with the hashes of persistent items.
Next to the preferences icon, is a the save icon. Click this to save KnockKnock's findings (as JSON):
Commandline Interface
KnockKnock now (as of version 2.0) can be run via the commandline. There are various benefits to this, including the ability to programmatically deploy and execute KnockKnock (perhaps on a regularly scheduled interval). Via the CLI, KnockKnock can also be executed with elevated privileges (i.e. sudo), which will ensure that KnockKnock will perform a more comprehensive scan of items for all users!
Execute the KnockKnock binary (note: specify the full path to the KnockKnock binary within its application bundle) with -h or
Knock Knock Mac Os Catalina
-help to display information about the self-explanatory commandline options:Knock Knock Mac Os X
Note:
To capture the output from KnockKnock, (as it writes to STDOUT), simply pipe it to a file out of your choice:
$ ./KnockKnock.app/Contents/MacOS/KnockKnock -whosthere > /path/to/some/file.json
To capture the output from KnockKnock, (as it writes to STDOUT), simply pipe it to a file out of your choice:
$ ./KnockKnock.app/Contents/MacOS/KnockKnock -whosthere > /path/to/some/file.json
FAQs
Q: KnockKnock found many applications, should I be worried?
A: No. KnockKnock simply enumerates items that are automatically started; either during startup, during login, or during another application's launch (e.g. browser extensions). Although signed-Apple items are filtered out by default, many legitimate 3rd-party items will likely be shown. Of course, the goal is that KnockKnock will also display any persistently installed malware.
Q: Ok, so how do I determine if something is malware?
A: By design KnockKnock itself doesn't try to determine if something is malware or not. However, since VirusTotal is fully integrated into KnockKnock, known malware will be detected (and highlighted in red). The remaining items that are not flagged can be manually examined. Perhaps google the hash of the file, run strings on it, or if you are really concerned about a specific item, email me at patrick@objective-see.com and attach the file :)
Q: When I run KnockKnock, why does it ask to access my downloads/desktop/calendar folder, etc?
A: As part of its enumerations, KnockKnock scans running processes and their dependencies. If a process has an item loaded from these locations, when KnockKnock scans it, it may generate an OS alert.
Q: Why does KnockKnock try to access the network?
A: When KnockKnock is started, it connects to Objective-See.com to check if there is a new version of the product. Specifically, it reads the file products.json, which contains the latest version number of KnockKnock. No user or product information is collected nor transmitted.
KnockKnock may generate network traffic related to its integration with VirusTotal. As described above, when a user clicks the 'virus total' button in the alert window, this will send generate a request which contains the file's path, name, and hash. Note that the automated version checking can be disabled via the 'disable update checks' option in KnockKnock's preferences.
Finally, KnockKnock also utilizes Sentry.io for crash detection which may generate network traffic related to crash reporting.
A: No. KnockKnock simply enumerates items that are automatically started; either during startup, during login, or during another application's launch (e.g. browser extensions). Although signed-Apple items are filtered out by default, many legitimate 3rd-party items will likely be shown. Of course, the goal is that KnockKnock will also display any persistently installed malware.
Q: Ok, so how do I determine if something is malware?
A: By design KnockKnock itself doesn't try to determine if something is malware or not. However, since VirusTotal is fully integrated into KnockKnock, known malware will be detected (and highlighted in red). The remaining items that are not flagged can be manually examined. Perhaps google the hash of the file, run strings on it, or if you are really concerned about a specific item, email me at patrick@objective-see.com and attach the file :)
Q: When I run KnockKnock, why does it ask to access my downloads/desktop/calendar folder, etc?
A: As part of its enumerations, KnockKnock scans running processes and their dependencies. If a process has an item loaded from these locations, when KnockKnock scans it, it may generate an OS alert.
Q: Why does KnockKnock try to access the network?
A: When KnockKnock is started, it connects to Objective-See.com to check if there is a new version of the product. Specifically, it reads the file products.json, which contains the latest version number of KnockKnock. No user or product information is collected nor transmitted.
KnockKnock may generate network traffic related to its integration with VirusTotal. As described above, when a user clicks the 'virus total' button in the alert window, this will send generate a request which contains the file's path, name, and hash. Note that the automated version checking can be disabled via the 'disable update checks' option in KnockKnock's preferences.
Finally, KnockKnock also utilizes Sentry.io for crash detection which may generate network traffic related to crash reporting.
Knock Knock Mac OS
